- Open Source CEO by Bill Kerr
- Posts
- Deel, Rippling & The History Of Corporate Espionage
Deel, Rippling & The History Of Corporate Espionage
A spy story of the grandest scale in the world of payroll management. 🕵🏻♂️
👋 Howdy to the 1,831 new legends who joined this week! You are now part of a 117,399 strong tribe outperforming the competition together.
LATEST POSTS 📚
If you’re new, not yet a subscriber, or just plain missed it, here are some of our recent editions.
💰 Early Entrepreneurship, Cash Management & Building Scrappy. An interview with Ben Döpfner, founder & CEO of Vesto.
🗺️ The Four Types Of Managers & How To Manage Them. A leadership performance matrix to assess your team.
🔐 Unfiltered: The Details Behind Vanta's Meteoric Rise. Vanta opens up about building a security game-changer.

PARTNERS 💫
Webinar: Transitioning to usage-based pricing with Hubspot's Sam Lee.
More companies are turning to usage-based pricing, but the challenge isn’t just whether to adopt it—it’s when and how to do it right.
Next Thursday March 27th, Sam Lee, VP of Pricing and Product Operations at HubSpot, and Metronome CEO Scott Woody are teaming up to share lessons and best practices for transitioning to usage-based and hybrid pricing. Plus, key pitfalls to avoid from Sam’s experience leading pricing teams and Snowflake and Hubspot.
Interested in sponsoring these emails? See our partnership options here.

HOUSEKEEPING 📨
Planning some leave in a couple of weeks time. It’s pretty draining at times running Athyna, while also pumping out these newsletter. As much as I love both projects, I am due for a well earned rest I think.
My plan is to head down to San Martin de los Andes, accompanied by my little perrito (Spanish for little doggy), Ziggy. |  |

BUSINESS STORY 🗞️
Deel, Rippling & The History Of Corporate Espionage
I grew up a big fan of Mad Magazine, and in particular a fan of their regular Spy vs Spy section. As I grew out of my early teens, I graduated to more adult spy escapades, highlighted—like a lot of kids my age—by countless hours of GoldenEye on the Nintendo 64. To me, Pierce Brosnan will go down as the equally worst, and best Bond of all time due to his underperformance in the movies, and outperformance in the video game respectively. Lately, I have actually taken to the British spy drama, Slow Horses, on Apple TV+. It’s a decent watch.
But nothing I have seen or consumed in spy-world prepared me for what I would see on Twitter on March 17, 2025, when Rippling CEO, Parker Conrad, announced that Rippling were suing Deel for ‘cultivating a spy at Rippling & orchestrating a long-running trade-secret theft.’ Corporate espionage of the B2B world.

Today then, off the back of this news, I plan to break down this aforementioned heist of insider information, along with the history of espionagus corporatus, and if you are lucky (and you are) a sprinkling of extra example of people taking the proverbial mickey out of their competitors. Let’s investigate.
What is ‘espionage’ anyway?
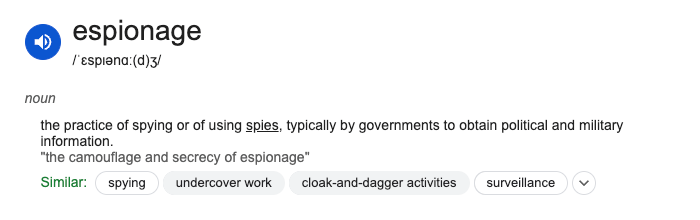
Espionage (/ˈɛspɪənɑː(d)ʒ/) as per Google’s definition is ‘the practice of spying or of using spies, typically by governments to obtain political and military information.’ Similar works include spying, undercover work, cloak-and-dagger activities. We all know this. It’s the stuff of Bond, James Bond. But how common is espionage, where did it start, and who employs it today?
Firstly, let me point out that as per Sun Tzu’s, The Art of War, there are five different kinds of spy: the local spy, the inside spy, the reverse spy, the dead spy, and the living spy. Below is a breakdown of each spy type and their modern day equivalent.
Type | Definition | Modern equivalent |
|---|---|---|
The local spy | These are hired from among local people. | Insiders who are already working for the enemy and secretly provide information. |
The inside spy | These are hired from among enemy officials. | A double agent in a rival company, an employee leaking secrets, or even corporate mole placements. |
The reverse spy | Enemy spies who have been captured and turned to work for you. | Competitor employees who get flipped, either by hiring them or coercing them into revealing secrets. |
The dead spy | Spies sent with false information, knowing they will be caught and feed misinformation to the enemy. | Controlled leaks, fake product launches, or misleading PR campaigns to confuse competitors. |
The living spy | Spies who gather intelligence and successfully return to report their findings. | Corporate intelligence operatives who gather data from conferences, trade shows, or through networking. |
The earliest documented spies appear in biblical texts, dating all the way back to approximately 1200 BCE. The Book of Numbers tells how Moses dispatched 12 spies into Canaan to gather intelligence before the Israelites attempted to settle the territory. Their mission was to assess the land, inhabitants, defenses, and resources.
The Persian also didn’t mind a bit of espionage (circa 522 BCE - 330 BCE) with the Achaemenid Empire under Darius I. King Daris, also known as Darius the Great, had an intelligence network called ‘The King’s Eyes and Ears.’ This was essentially one of the first recorded secret services.
Corporate espionage, though, may have started truly with The British East India company (1600s-1800s), who used spies to undermine competitors (like the unoriginally named Dutch East India Company) and even whole governments.
British East India Company.
Nikola Tesla and Thomas Edison were said to have planted spies on one another, the KGB infiltrating American companies through the Cold War, and China today is probably spying on you and your technology right now. The list goes on. Espionage today is not seen among the fictional Jason Bournes of the world. It’s alive and well. And no more so it seems—can’t believe I am about to write this—than in the world workforce management platforms.
A history of beef
Before diving headfirst into the corporate espionage, it behooves us to take a quick detour down Rivalry Road. The two companies in question, Rippling and Deel, already had a nice little competitive streak going, before it started to get ugly late last year when Rippling created a landing page with the header; “Don’t Buy Snake Oil” in reference to Deel’s security and compliance claims. They even went as far as to program an old school Nokia 8210 style game of snake. Each time you were successful with your snake directing, a new level of Deel’s (supposed) falsehoods would be presented to you. Pretty wild really.
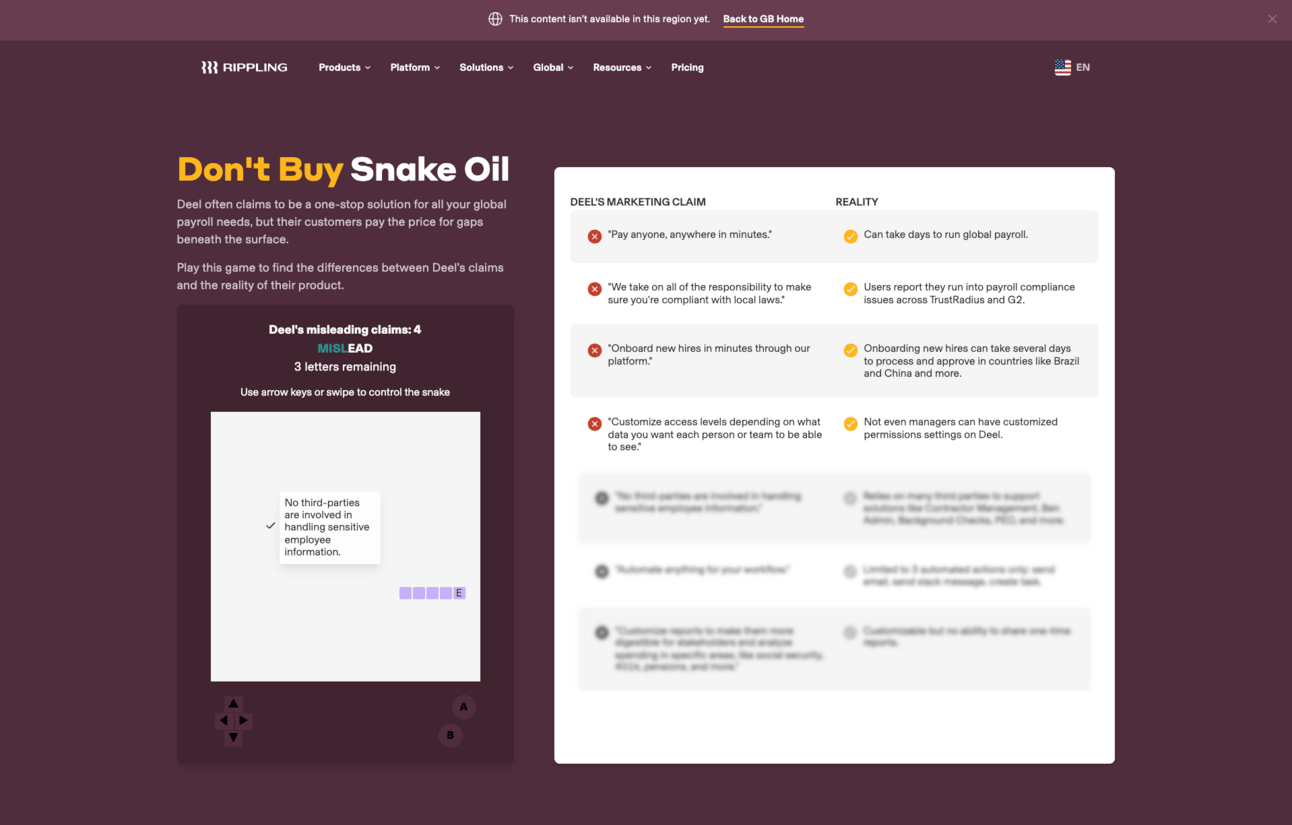
Source; Rippling’s snake oil game.
Things turned uglier again when sales leader at Deel, Chris Lee, told Rippling to “suck a d*ck” in their chatbot thread, leading the COO of Rippling to not only share this on Twitter but share Chris’ email, phone number and all. It’s not nice to tell someone to S-a-D, but in this case, I kinda feel like it was warranted. This whole thing makes Rippling look terrible.
Am I understanding this right? Rippling…
…called Deel “snake oil”
…then made a marketing campaign with a game and Deel’s logo as the snake
…with an automatic chat bot on the page
…and posted a Deel employee’s info when they got angry at them in said automatic chat?wtf?
— Theo - t3.gg (@theo)
12:05 AM • Dec 4, 2024
The Deel is better than Rippling / Rippling is better than Deel comparison pages are actually value too. Carbon copies of one another. Kinda as if they just hit their version of the ‘invert colours’ option on their iPhone. Who’s really better is anyone’s guess.
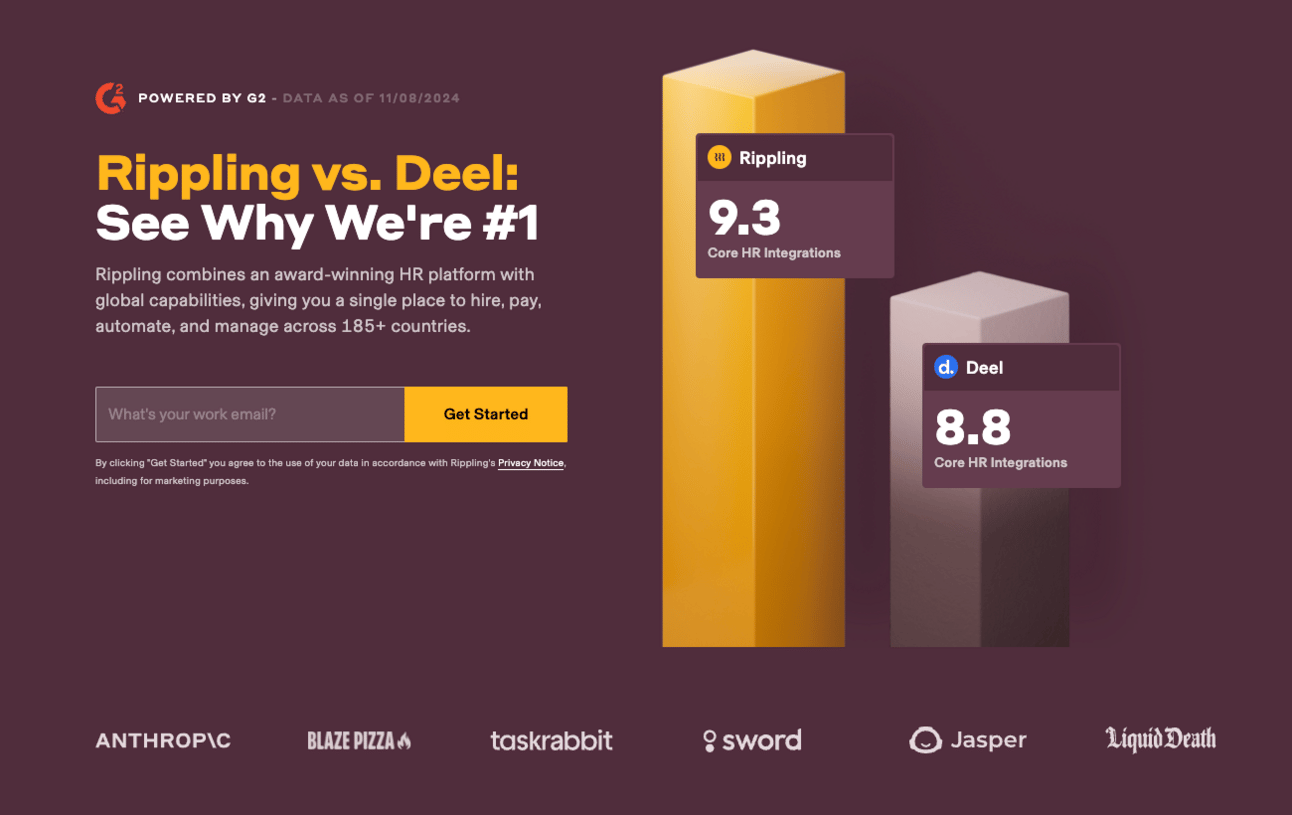 |  |


Deel vs Rippling
And now we come to today’s main event. The allegations and incoming lawsuit from Parker Conrad and his $13 billion dollar Rippling, to the $12 billion dollar firm by the name of Deel, on the grounds of corporate espionage. “Our lawsuit alleges Deel cultivated a spy at Rippling & orchestrated a long-running trade-secret theft,” Parker cited in his March 17 tweet.
The Rippling founder claimed that Deel had embedded a spy inside of their organisation to mine their trade secrets. And that the spy searched for the term ‘deel’ a legendary 23 times per day while working as a Rippling employee.
Rippling sued @deel today. Our lawsuit alleges Deel cultivated a spy at Rippling & orchestrated a long-running trade-secret theft. The spy searched “deel” in our systems 23 times per day on avg, letting him spy on Deel’s own customers who were considering a switch to Rippling.
— Parker Conrad (@parkerconrad)
12:42 PM • Mar 17, 2025
Why would Deel go to the lengths of doing something like this I bet you are wondering? Well—simple really. B2B software accounts can be very spicy at the larger end of town. I asked ChatGPT 4.5’s to do some deep research for me on the lifetime value of an enterprise client and it came back with an estimate of several millions of dollars for both firms.
Think on what a successful spy might be able to do inside of Rippling. A spy could find pitch decks for new deals in pipeline to leverage against at Deel. They could go snooping out for clients that are looking to defect from Deel to Rippling. And conversely, they could find customers that are unhappy with their current Rippling experience and report back to prospect heavily towards those accounts.
Not to mention GTM strategies, corp dev, unhappy executives and teams to poach from, the list goes on and on. In the same ChatGPT thread, I asked how much value Deel could have siphoned from Rippling over the course of a 12 month period and it came back with an estimate several to tens of millions. I think that could be massively underselling it.
So how did Rippling find this alleged double agent in their midst? Simple. They set what is commonly referred to as a ‘honeypot.’ Specifically, a fake Slack channel supposedly filled with embarrassing dirt on Deel. Get a load of this passage from the 50 page official complaint document. |  |
Astoundingly, this hijacking of Rippling’s most prized data appears to have been orchestrated by Deel’s senior leadership. The smoking gun came earlier this month, when Rippling set forth a test, or what is known by security professionals as a “honeypot.” Rippling knew that Deel was most likely to activate its spy if faced with potentially damaging press, and indeed, that is how the spy originally revealed himself.
So, to confirm Deel’s involvement, Rippling’s General Counsel sent a legal letter to Deel’s senior leadership identifying a recently established Slack channel called “d-defectors,” in which (the letter implied) Rippling employees were discussing information that Deel would find embarrassing if made public. In reality, the “d-defectors” channel was not used by Rippling employees and contained no discussions at all. It had never been searched for or accessed by the spy, would not have come up in any of the spy’s previous searches, and the spy had no legitimate reason to access the channel. Crucially, this legal letter was only sent to three recipients, all associated with Deel: Deel’s Chairman, Chief Financial Officer, and General Counsel (Philippe Bouaziz), Deel’s Head of U.S. Legal (Spiros Komis), and Deel’s outside counsel.
Neither the letter nor the #d-defectors channel was known to anyone outside of Rippling’s investigative team and the Deel recipients. Yet, just hours after Rippling sent the letter to Deel’s executives and counsel, Deel’s spy searched for and accessed the #d-defectors channel—proving beyond any doubt that Deel’s top leadership, or someone acting on their behalf, had fed the information on the #d-defectors channel to Deel’s spy inside Rippling.
That, ladies and gentlemen, is what in the spy business we call a good old fashioned honeytrap.
Once busted, when lawyers later tried to confiscate his phone under court order, the alleged oath-breaker fled into a bathroom, locked himself inside, and seemed to try flushing his phone down the toilet rather than hand it over. He then stormed out, ignoring legal warnings, declaring he’d "take the risk," and vanished.
“Weeks after Rippling is accused of violating sanctions law in Russia and seeding falsehoods about Deel, Rippling is trying to shift the narrative with these sensationalized claims,” a spokesperson said in a statement provided to TechCrunch. “We deny all legal wrongdoing and look forward to asserting our counterclaims.”
Athyna’s espionage à trois
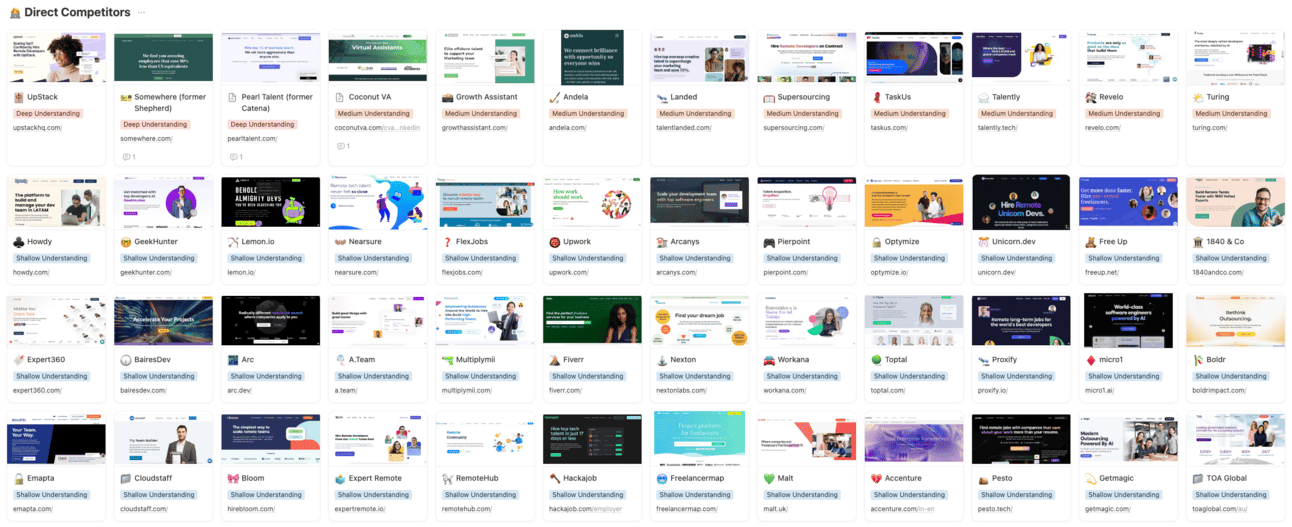
I’ll admit it. I see value in corporate espionage. I’m not sure I’ll be embedding any insiders in the organisations of our competitors anytime soon, but I went as far as to build a somewhat robust competitive intelligence program at my startup, Athyna. We have internal databases tracking 50+ direct and indirect competitors. I think it’s a super smart practice. Especially if you in a somewhat commodified space.
We don’t spend too much time on this for the most part but every so often we will do a deep dive on a company, and try to find out how they message, what is their offer, how and where they hire, and more. In our databases we categorise companies by having deep, medium or shallow understanding.
*Note: I was told that what I am about to tell you in the next few lines is a bad idea, that it will make me look bad, but I am going against that recommendation in the interest of being fully open sourced, as is the spirit of this newsletter.
We have even gone as far as to create fake profiles to take demos, get sales decks and ask questions to some of our more senior competitors. I want to see what makes them tick.
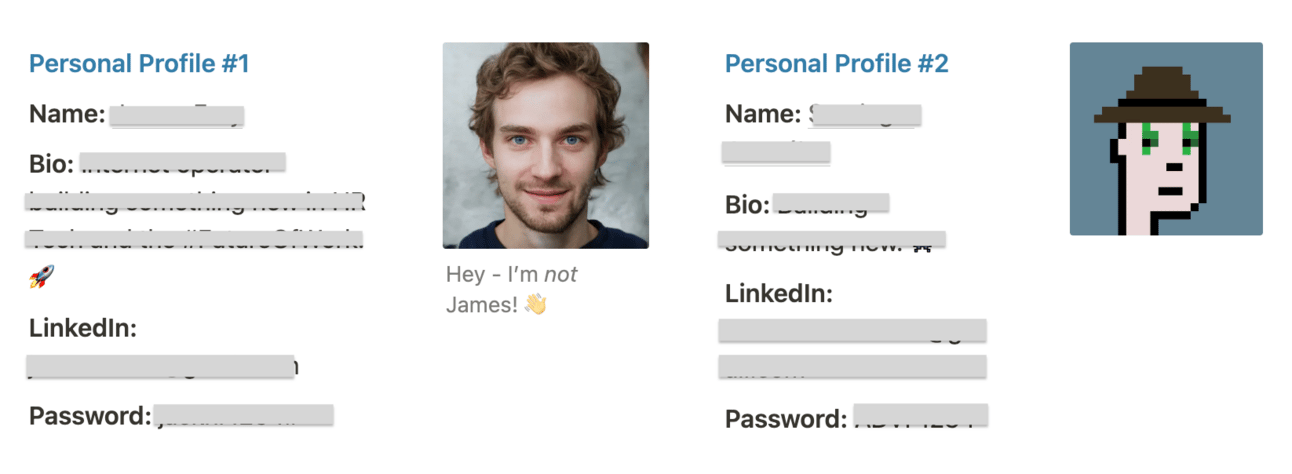 |  |
These types of initiatives are also engaging for the team. It’s as if you are playing a little spy game yourself. An us versus them drama. I think it’s healthy and for the most part, I don’t wish any harm to our competitors. Sure, there are one or two that I have sworn to myself that I will personally burn to the ground, but for the most part, I see it as healthy competition.
*Note: I was also told to take that ‘burn them to the ground’ line out too. Because it might make me look like a psycho, but the truth is, I kinda am a psycho, and I do want to burn a couple of their business to the ground.
My personal intelligence muse
The most interesting person I’ve ever heard talk about this type of competitive intelligence program is Patrick Campbell, the founder and CEO, of ProfitWell, which was recently acquired by Paddle for $200M. Patrick has the most detailed guide in the world when it comes to competitive intelligence. And let me be clear when I say I’m not exaggerating when I say that. It’s a 20,000 word deep dive, highlighting everything from marketing mindshare and resource strength, to using a market command matrix and more. The guy is literally the Picasso of intel.
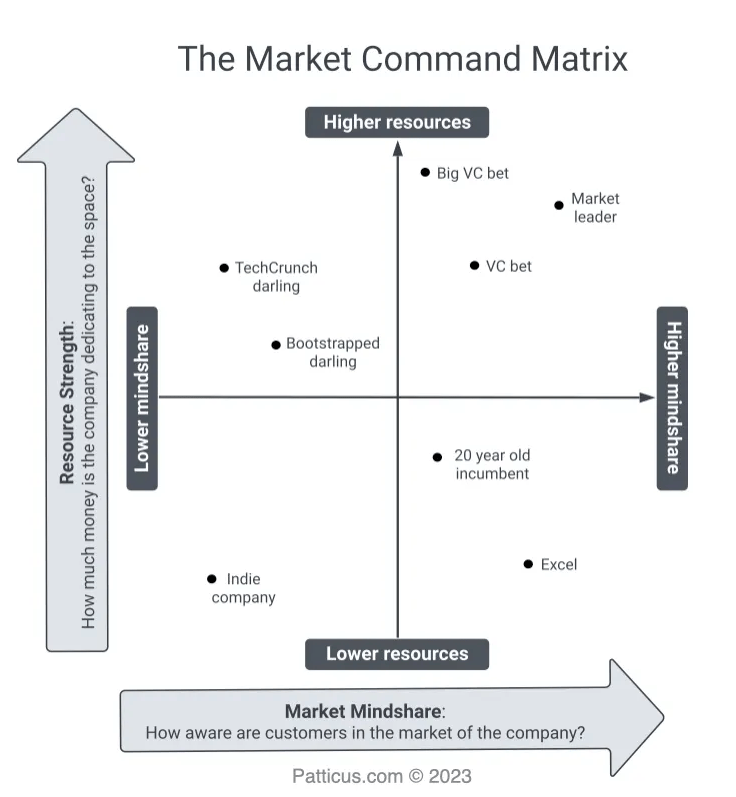 | 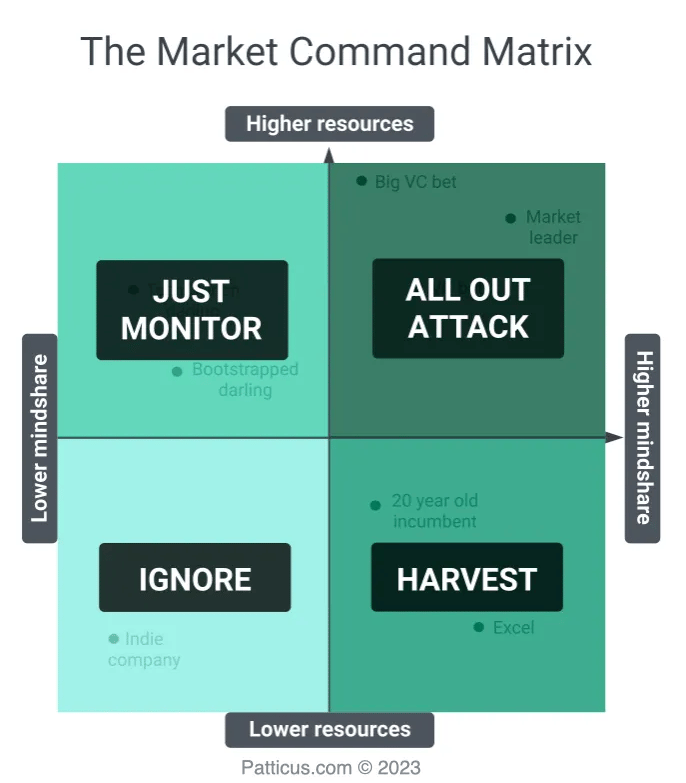 |
Patrick claims that any competitor intelligence program (even the US government’s) has three main parts: 1) reconnaissance, identifying your competitors, 2) monitoring and extracting intel, and 3) intelligence operations, playbooks to attack and defend.
The what | The why / how |
|---|---|
Reconnaissance and identifying | Who exactly are you competitors? Here we’ll answer that question by automatically creating your market’s Market Command Matrix. From there you’ll know exactly who to worry about, spend time on, and ignore. |
Monitoring and exacting | Once we know who we should be tracking, we need a system for collecting research and intelligence on those competitors. Monitoring these competitors builds your judgement and market instincts to properly deploy the playbooks for siphoning revenue from competitors. |
Intelligence operations | Knowing who to track and monitoring them is just the first piece of the puzzle. Now we need to deploy our revenue playbooks at the right time. |
The details above are lifted directly from Patrick’s resource, so full credit to him. If you are interested, I really recommend to check it out. In what I swear is totally coincidental news, I am doing a webinar next week with the team at Paddle, who acquired Patrick’s company. We’ll be talking about how I use the tool he built, ProfitWell metrics, to tell data driven revenue stories to our team.
💡 Note: Sorry about that, honest pitch I swear. If this is cool to you, sign up to grab a spot here.
Other famous espionagery
In honour of Deel’s attempt to steal corporate secrets from a competitor, here a chronological list of other recent attempts to steal the ‘secret sauce.’ Or in one case, quite literally the 11 herbs and spices.
Kodak vs. Fuji, 1980s–1990s: Kodak accused Fuji of aggressively spying on its film-development technology. Though no clear legal winner emerged, their rivalry was marked by bitter accusations and prolonged suspicion.
Volkswagen vs. General Motors, 1993–1996: VW poached José Ignacio López, a high-level GM executive, who brought along confidential internal documents. GM sued, resulting in a $100 million payout and López's resignation.
Gillette vs. Schick, 1998: Gillette accused Schick of deploying private investigators to obtain intel on their top-secret razor developments. The bitter dispute led to reciprocal lawsuits, public embarrassment, and damaged reputations.

Boeing vs. Lockheed Martin, late 1990s–2006: Boeing stole rocket-launch secrets from Lockheed Martin to secure lucrative NASA and Air Force contracts. Boeing ultimately paid a record $615 million in fines.
Coca-Cola vs. PepsiCo, 2006: Coke employees tried selling secret recipes and proprietary documents to Pepsi. Surprisingly ethical, Pepsi reported them, leading to an FBI sting operation and multiple arrests.
Hewlett-Packard board spying scandal, 2006: HP hired private investigators who illegally obtained phone records of board members and journalists to root out corporate leaks. The scandal caused public backlash, resignations, and hefty fines.
Monsanto seed espionage, 2013–2016: Employees from a Chinese agricultural company attempted to steal genetically engineered corn seeds from Monsanto’s U.S. fields. The spies were caught and sentenced to prison, spotlighting the seriousness of agricultural espionage.
Uber vs. Waymo (Google), 2017: Waymo engineer Anthony Levandowski allegedly took thousands of confidential files when joining Uber’s self-driving division. After heated legal battles, Uber paid Waymo $245 million in equity to settle.
Kentucky Fried Chicken’s secret recipe, various attempts: KFC’s famous blend of ‘11 herbs and spices’ is notoriously protected. In 2001, the company sued individuals attempting to sell an alleged stolen recipe online.
Summary
And that’s the story of what might be the juiciest startup story since the Sam Altman x OpenAI firing / rehiring bonanza of late 2023. It really is quite juicy for the world of the startup nerd. This tweet I found recently sums it up best.
Rippling vs Deel is like Kendrick v Drake for people incapable of holding a conversation at a party
— Isaiah Granet (@zaygranet)
6:49 PM • Mar 17, 2025
So go out there and spy nicely my founder friends. And if you don’t decide to play nicely, make sure that whatever it is you do, you do it so extremely that they will make an HBO drama out of it someday. Cheers.
Extra reading
El Ascenso De Duolingo (The Rise Of Duolingo) - October 24, 2024
Mario, Luigi & The Long History Of Nintendo - November 17, 2024
Neumannomics: A Deep Dive - January 30, 2025
And that's it! You can follow me on Twitter and LinkedIn and also don’t forget to check out Athyna while you’re at it.

BRAIN FOOD 🧠
I just watched a TED talk on a topic I hadn’t seen so much buzz around, and thought I should share it. This one is about AI, and how AI models are built using unlicensed creative work—music, writing, art—without permission or payment.
Ed, the guest speaker, makes a strong case for why artists and writers should actually get compensated for the use of their work and he offers a pretty reasonable fix. If you’re a creator yourself or you’re into the industry, go give this one a watch.

TWEETS OF THE WEEK 🐣
SO THERE ARE THESE TWO HR SOFTWARE COMPANIES CALLED DEEL AND RIPPLING. THEY HATE EACH OTHER. THEY’RE LIKE THE HARKONNENS AND ATREIDES OF PAYROLL. RIPPLING JUST FOUND OUT DEEL HAD A SPY IN THEIR OFFICE. THEY SET UP A FAKE SLACK CHANNEL TO CATCH HIM, BUT HE LOCKED HIMSELF IN A… x.com/i/web/status/1…
— Robert Sterling (@RobertMSterling)
1:41 PM • Mar 18, 2025
This timeline is hard to understand. Just nuts.
— Sam Parr (@thesamparr)
3:42 PM • Mar 19, 2025
Remember. We all have to start somewhere.
— Bill Kerr (@bill_kerrrrr)
1:28 PM • Jun 27, 2024

TOOLS WE USE 🛠️
Every week we highlight tools we actually use inside of our business and give them an honest review. Today we are highlighting Attio—powerful, flexible and data-driven, the exact CRM your business needs.
See the full set of tools we use inside of Athyna & Open Source CEO here.

HOW I CAN HELP 🥳
P.S. Want to work together?
Hiring global talent: If you are hiring tech, business or ops talent and want to do it for up to 80% off check out my startup Athyna. 🌏
Want to see my tech stack: See our suite of tools & resources for both this newsletter and Athyna you check them out here. 🧰
Reach an audience of tech leaders: Advertise with us if you want to get in front of founders, investor and leaders in tech. 👀
 |





Reply